#1 Rated MFT Solution for Automating, Simplifying, and Streamlining File Transfers
Is your file transfer solution keeping you from moving data at the speed your business requires? MFT solutions enable you to quickly connect to internal systems and trading partner ecosystems, allowing your business to move sensitive data and govern all exchanges.
With Cleo's secure, reliable, and scalable MFT solution, you'll be able to support any secure protocol and share files with any trading partner, without the need for programming or special skills.
Connect to Your Partners & Infrastructure
CIC MFT provides a robust solution to onboard and manage partners as you grow your business. Quickly onboard partners into the platform, and more importantly manage and provide insight. CIC MFT offers Partner Management, allowing you to associate partners or business connections across the platform in an easy to use interface. Manage partner details, including identifies, contact information, and all associated connections.
Additional partner connectivity capabilities:
- Modern storage options: Azure, S3, GCP, Database, Cloudera, JMSQueue, SMB, NFS to connect partners and hybrid infrastructure
- Advanced Router Connector: Route payload based on content coming from or going to your partners easily with CIC MFT's Advanced Router Connector
- Reduce Onboarding Time: Quickly onboard partners with a single connection that supports FTPs/SFTP/HTTPs (Portal) with Transfer Reporting
Automate & Scale Your File Transfer
You have a lot of automated processes that can be very complex, and having a solution that can integrate with those is key to driving your success.
CIC MFT automation capabilities:
- Complex schedule automation (including event-based i.e. envoke a javascript when a file is received)
- Partner management: associate specific connections with your different partners to automate actions & routing
- Advanced support for high availability and disaster recovery to enable completely automated synchronization with synchronization monitoring
Enable Complete MFT Security and Governance
The CIC MFT Solution provides extensive features and functionality to secure your file transfer environment and govern your trading partner community.
Security capabilities:
- Multi-Level user access with support for LDAP/AD integration including SSO
- Perimeter layer security model
- Highly varied algorithm support for any platform compatibility
- Connection pool-based system with support for forward, reverse, and forward-reverse proxy
- Multi-protocol support for proxy integration
- IP filtering capability
- Dynamic Black Listing, manual or automatic responsiveness
- PGP and XML encryption handling capabilities
- TCP port usage report to better understand how to configure firewalls to allow connections in or out
Remove Service Complexity and Gain Ease of Use
CIC MFT was built to be easy for you to use. The MFT solution provides complete protocol support, security, end user authentication/ single sign on, and visibility/ dashboards/reporting.
What makes CIC MFT so easy to use?
- Multi-protocol support
- Natively available protocol set (18 total including file based, message based and database integration)
- Seamless setup for connections
- Single point access management
- Single integrated solution for file transfer and visibility
- Centralized certificate management
- Preconfigured hosts
- User-friendly Web administration
View and act on your critical data with...
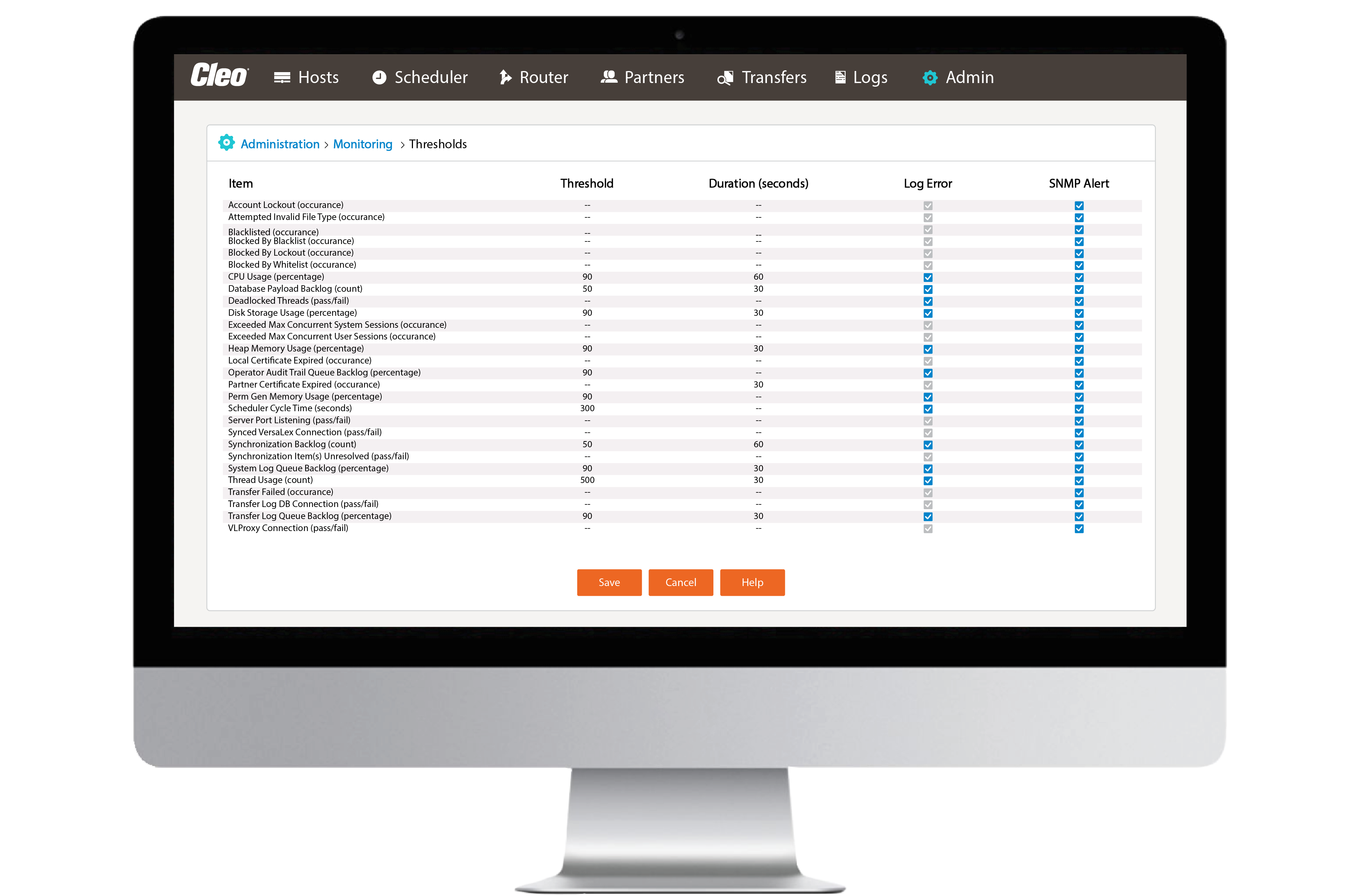
Monitoring and alerting
Monitor system and data health as data moves through your infrastructure, with monitoring modules and pre-built libraries that can be configured to business needs.
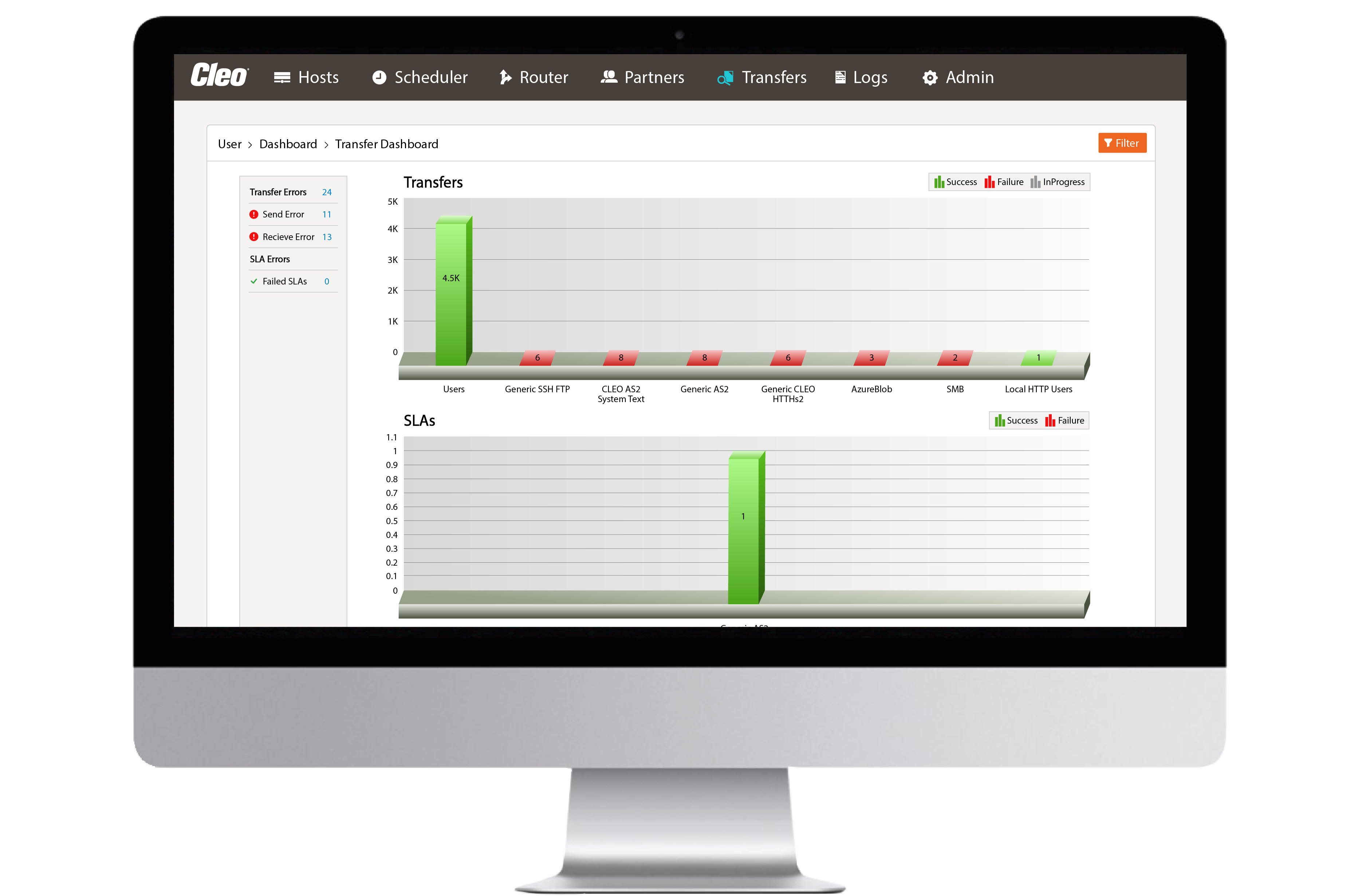
Centralized and holistic visibility
Gain better transactional visibility for business users in order to make confident critical business decisions faster than ever, with dashboard views for all system activity.
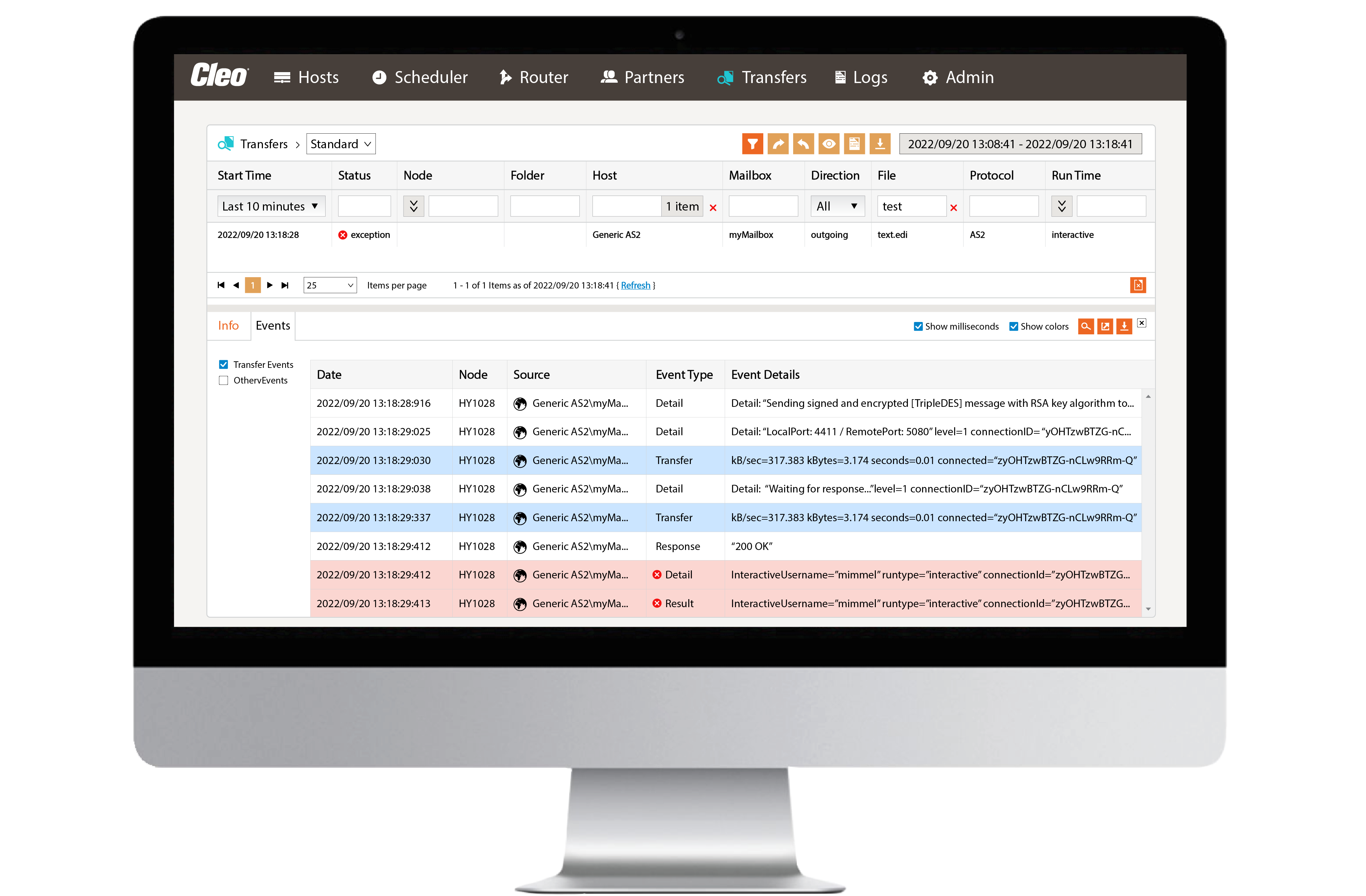
Issue identification
Equip your team to proactively solve issues before they become problems, with trading partner level monitoring and alerting, centralized log aggregation and incident tracking, and more.

Expect file transfer perfection with cloud certified MFT expertise
Cleo is committed to providing high-quality products and services. Cleo Integration Cloud is secure and tested against industry standards and is designed for data security and process integrity.
Read user reviews
- Ready for real-world results? Read our customer reviews and see why we’ve been rated a G2 Leader for 4 consecutive years.
How Precoat Metals enhanced its B2B managed file transfer with Cleo
A steel-coating supplier, Precoat Metals relies on secure MFT and EDI to communicate with manufacturers, because not just any file transfer software will do. Learn how Precoat Metals leverages Cleo's managed file transfer solution to enhance those critical communications and accommodate its customers' various protocol needs.
Learn more about file-based/MFT integration
Frequently asked questions
Don't let unanswered questions hold you back from streamlining your data exchange. Dive into FAQs, where we crack the code on the most common MFT questions!
What is managed file transfer?
Managed file transfer (MFT) is a secure solution that provides reliable inbound and outbound file transfer for organizations, whether within their private network or to external users. The "managed" aspect of MFT refers to the ability of the solution to automate, simplify, and streamline data transfers across one or several organizations, within a private network, or with external users.
Managed file transfer offers many features that ensure secure and reliable file transfers, including encryption, user authentication, and audit trails. These features are crucial for organizations that must comply with regulations like PCI DSS or HIPAA. MFT helps guarantee the security and integrity of sensitive data.
How does managed file transfer work?
1) The MFT file transfer application sends original files. Typically, depending on the quantity and size of the files being transferred, this procedure might range in difficulty. However, MFT guarantees rapid and safe data transfer.
2) The files are encrypted by the MFT solution. Once the transfer has been established, the MFT solution receives the data and secures it in a number of ways. Most MFT employs one of many protocols to encrypt the transfer and AES ciphers that comply with FIPS 140-2 to encrypt the files. Some methods also permit file compression using zip.
3) The data delivery is received by the recipient. Once the MFT file transfer has left your server, it is transferred to the address you provided, such as an email address, a specific folder on another server, etc. At this point, the file can then be decrypted by the recipient.
4) In addition, many file transfer solutions can be helpful to set up bulk or repeating transfers using auto-resume to ensure files arrive at their destination without the need for troubleshooting, as well as creating logs to get an overlooking view of all file transfers (even weeks/months after they're finished).
Why use managed file transfer?
In the modern landscape, safeguarding sensitive data is crucial, both while it is in transit and while it is stored. One of the various file transfer choices is managed file transfer. But it stands out from other file transfer strategies as a centralized means for securely automating, encrypting, and transmitting data from one location to another. Using controlled file transfer may be beneficial for your company if it must:
- In the cloud or on-premises, share data with internal and external stakeholders.
- File transfers made by your company should be audited or watched over.
- Comply with all rules and legislation pertaining to data security.
- Change the way you deliver data to a safer method.
- Use flexible procedures that can resume on their own, limit manual error, and handle outages.
For your organization to have the flexibility it needs to transfer files securely, some MFT solutions include extra features that let you combine data flow across the cloud and online apps you use every day. These solutions can be deployed on-premises, in the cloud environment, or as a SaaS solution.
What are the benefits of MFT solutions?
Data security: Eliminate security gaps and governance challenges with structured access control.
Consolidation: Consolidate all integration processes onto a single platform for central control and management.
Collaboration: Connect internal and external file sharing and collaborative workflows.
Auditability: Track all files that are received by or sent from your organization.
Process automation: Build, transform, and automate integrations by leveraging APIs.
What are features of top MFT solutions?
Flexible Deployment Options: MFT vendors that don’t support flexible deployment options do not embrace modern IT strategies, so it’s critical an MFT solution can be launched on-premise, in the cloud, or both.
Comprehensive Audit Functionality: A full audit trail of a file’s life cycle is required to maintain government and industry compliance and often to meet SLAs and KPIs. A must-have for many organizations, leading MFT solutions eliminate the manual data fetches for auditing/reporting and automate the tracking process so you know every aspect – when it was sent and received, who touched it and when – in case of an audit.
Non-Repudiation Capabilities: Non-repudiation is proof that what was sent by a certain system or person was actually received by another system or person, and that it is indeed the same file. This ensures integrity of the document. MFT solutions do this via digital signatures in combination with cryptographic data hash functions, such as the SHA-1 and SHA-2 algorithms. While required in many industries, including healthcare, banking, insurance, and securities, non-repudiation capabilities are critical to knowing your data sets are authentic and will benefit every organization doing digital business.
Complete Security and Governance Enablement: The best MFT solutions provide extensive features and functionality to secure your file transfer environment and govern your trading partner community.
- Secure access control via LDAP
- Enable antivirus and content scanning through ICAP
- Authorization (OAuth 2.0), authentication (SAML), encryption, certificate management
- Perimeter layer security with bidirectional proxy architecture
- Reporting, audit trails, and visibility dashboards
Scalability: File transfers could change from time to time. Later on, you might require more file transfer bandwidth, more features and modules, or a larger user base. Ensure that the MFT solution you choose can adapt to the development and changes in your business.
Customization Without Going Over Budget: Choose the software package that best suits your company. Make sure you can purchase more software without paying a fortune.
Why do large enterprises tend to choose CIC MFT over other managed file transfer options?
CIC MFT uses a centralized, enterprise-level approach to automate, secure, and govern all managed file transfers moving throughout the business ecosystem. Cleo's MFT solution enables the data protection and data security large enterprises need for all system-based and ad hoc file transfers.
Rapid connections
Set up connections and start transferring files in hours instead of days, or even weeks.
Multi-protocol support
Support all secure protocols required to handle data exchanges with any internal and external system.
Compliance
Gain real-time visibility, complete control, and governance to help meet all compliance mandates.
File acceleration
Move data, of any size or volume, 3.5x faster than competing solutions.
Flexible deployment
Deploy on your cloud or the Cleo Cloud platform, with the flexibility to self-manage MFT processes, or have Cleo manage them for you.
Browse MFT resources
Browse our 3 most popular resources to learn more before meeting with us.