Cleo Integration Cloud
Quickly onboard and automate every API and EDI integration directly into any back-office application and gain complete end-to-end visibility for every B2B transaction.

Faster trading partner onboarding
Get 10x faster trading partner onboarding by leveraging the Cleo Network and pre-built EDI and API integrations to automate direct integrations into your back-office application.
Your company can handle onboarding internally with our self-service approach, or it can outsource onboarding to our 24/7 managed services team.
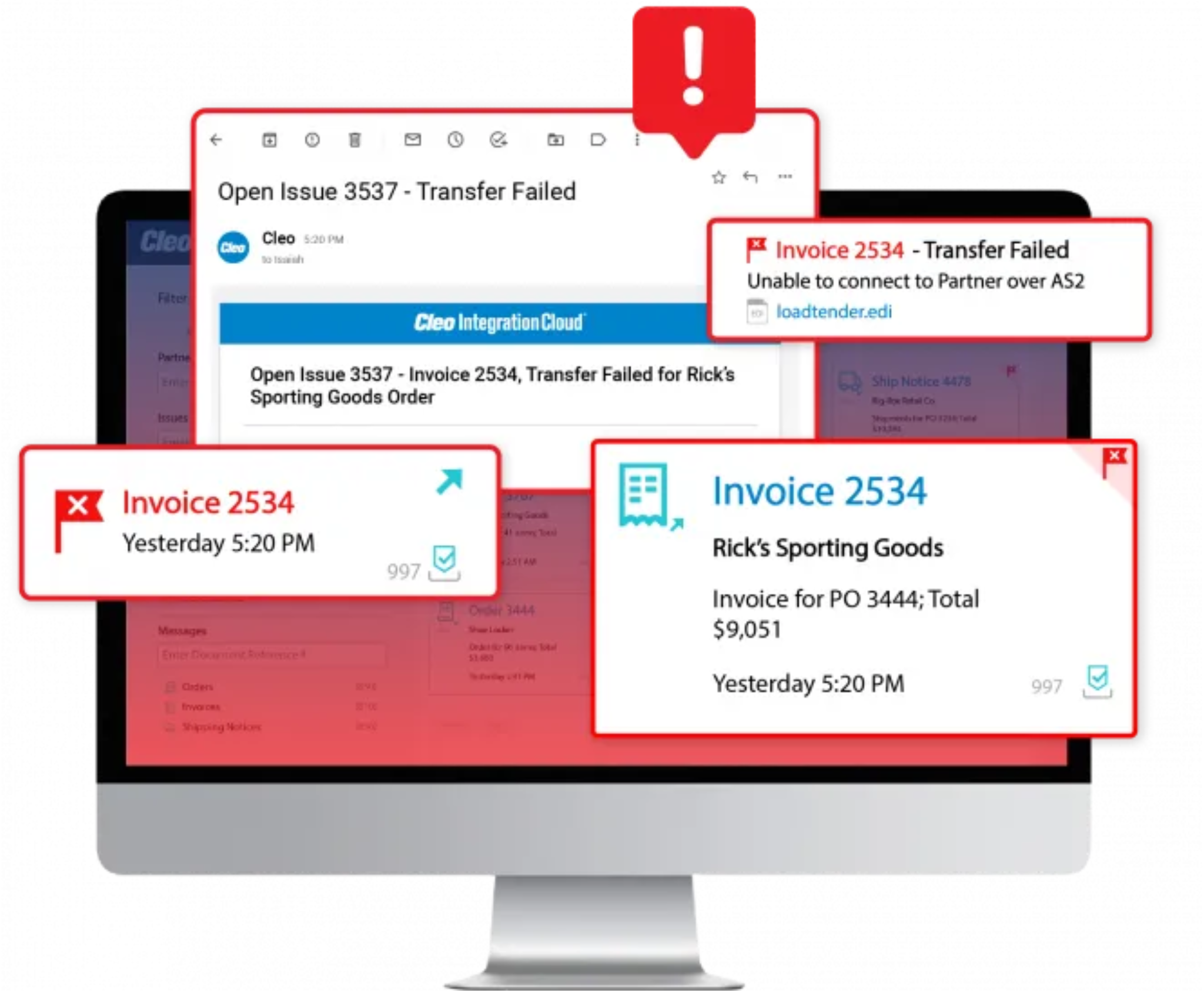
Rapid error resolution
Improve trading partner scorecards by eliminating errors and chargebacks through proactive monitoring, alerting and insights.
Drill down into any integration flow or transaction to swiftly identify where and why an error is occurring—allowing your team to resolve the issue, or leverage Cleo’s global team of experts to ensure errors are fixed quickly before they cause disruptions.
Automate EDI & API transactions
Automate and orchestrate every API & EDI transaction to avoid slow response times, manual data input errors, integration complexity, bottlenecks, missed SLAs, and violation fees.
Integrate seamlessly with any back-office system, from ERP and TMS to WMS and beyond, for true end-to-end efficiency.
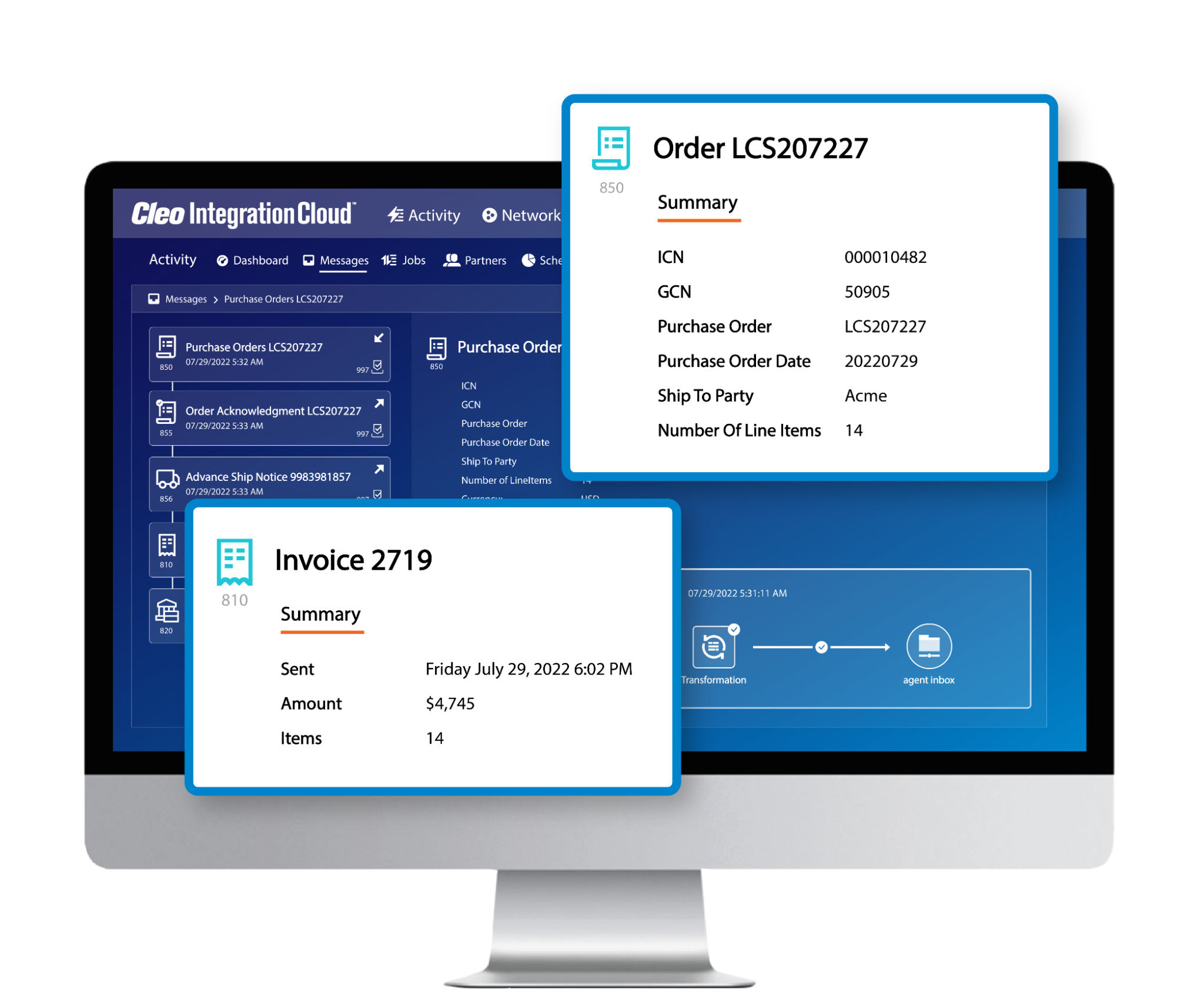
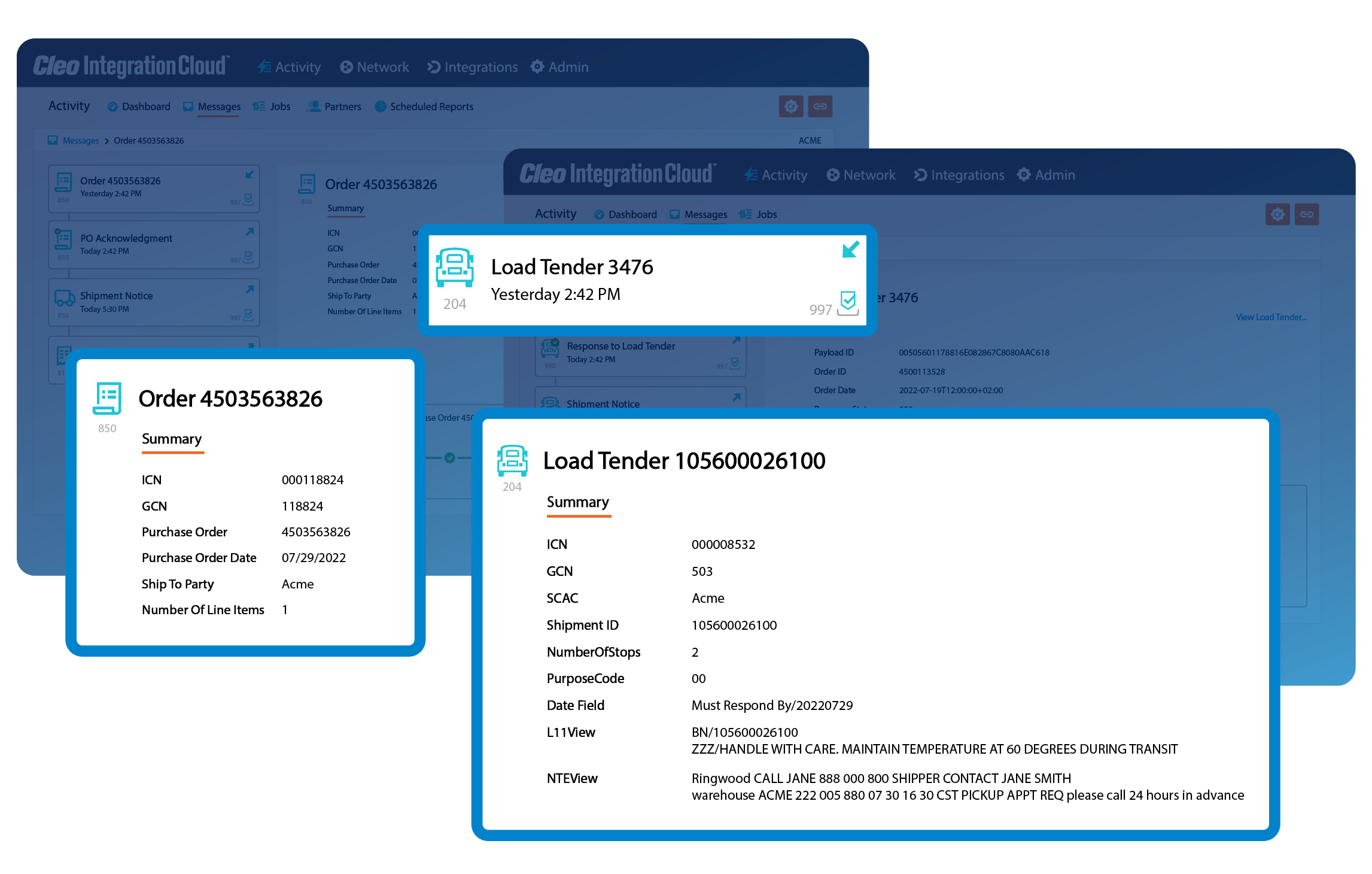
Complete business flow visibility
See the bigger picture by getting a bird's eye view of your business processes. Correlate invoices with orders, load tenders with responses, and easily search for critical transactions.
With complete business flow visibility, you can see what's happening, find what you need, and make informed decisions faster.

End-to-end back-office system integration
Create complete, end-to-end B2B integration flows to any ERP, TMS, WMS or other back-office systems by leveraging APIs, integration connectors, or pre-built integrations.
Enable secure integrations into on-premise environments where APIs do not exist with a lightweight, headless agent.
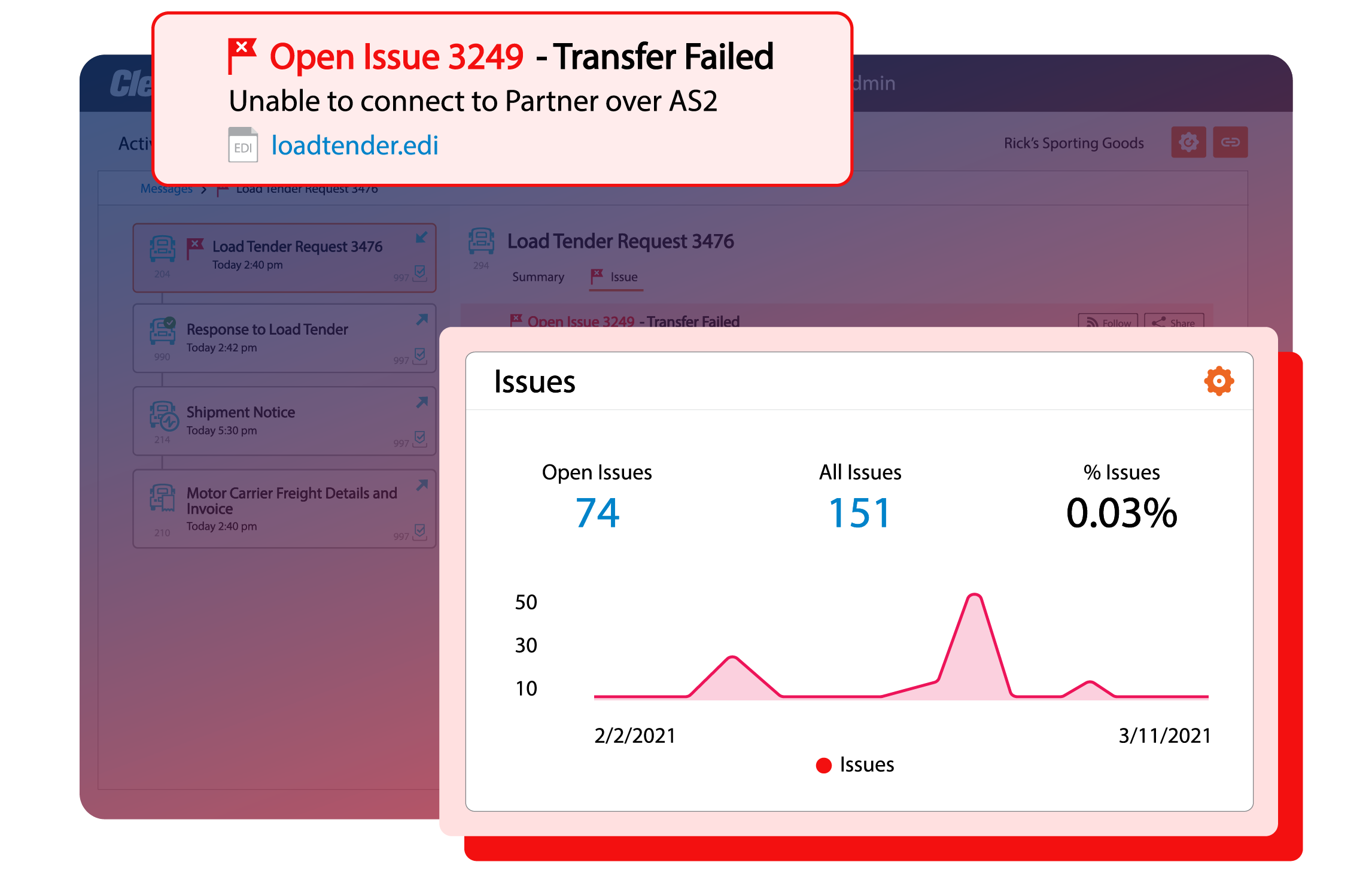
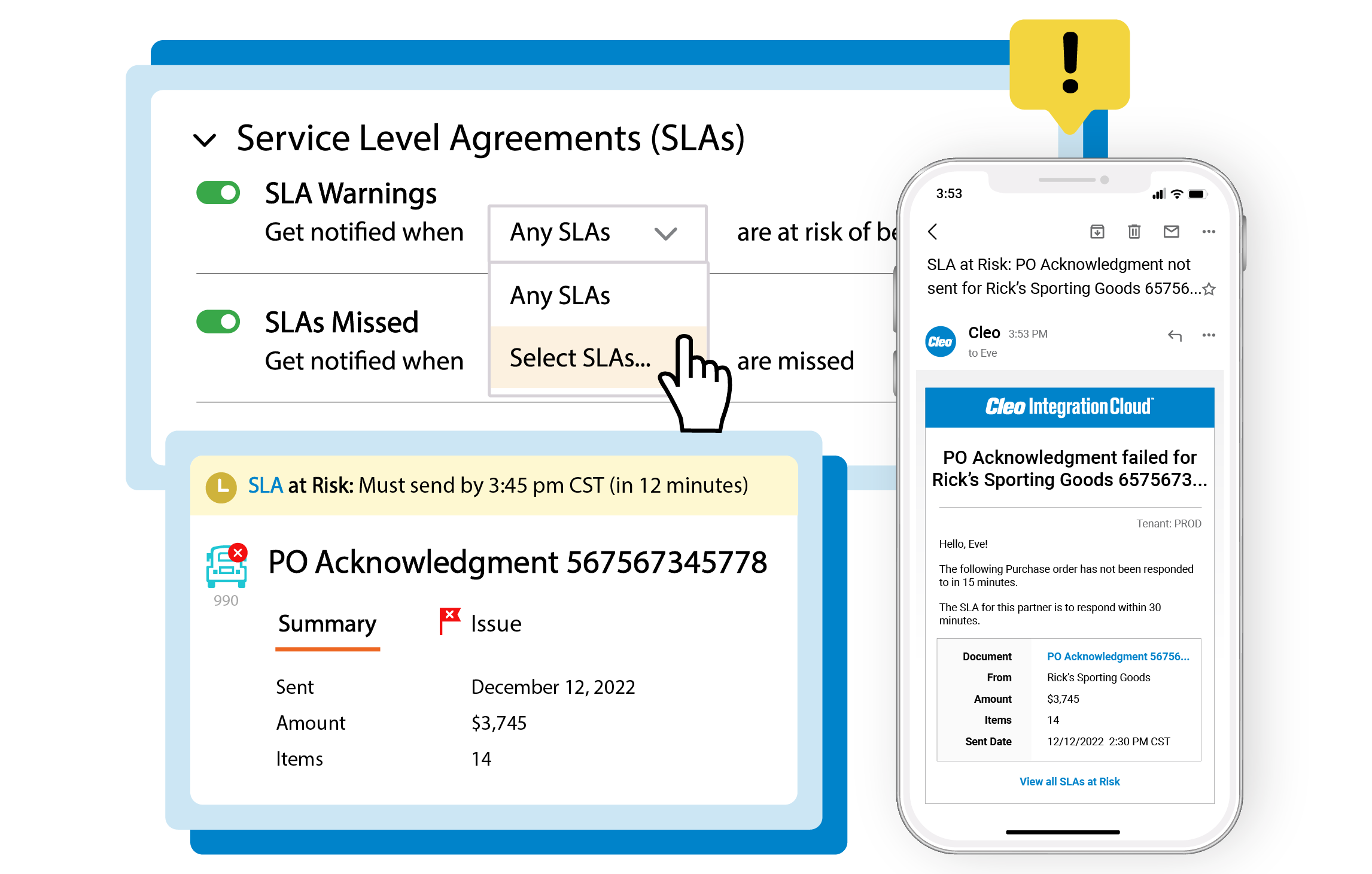
Real-time business insights
Configurable dashboards and alerts for any technical or business user for real-time insights across every B2B transaction from orders and load tenders to acknowledgements and invoices.
Eliminate the risk of chargebacks or fines from missed transactions, SLAs, KPIs, or business commitments.

eCommerce & marketplace integration
Grow your sales with an integration platform designed to power direct-to-consumer, omnichannel, and digital shopping experiences.
With Cleo’s vast protocol support, pre-built integrations, and business process automation, your business can quickly integrate with any eCommerce or digital marketplace.
Thousands of organizations are achieving astonishing results with Cleo Integration Cloud
Cleo delivers faster implementation, more comprehensive end-to-end solutions, and superior support vs. black-box integration technology and traditional managed service providers.
10x
94%
80%
One platform to meet all your B2B needs
Explore the platform for yourself to see how simple B2B excellence can be. Choose from any one of the walkthroughs.